Get Ssh Keygen Source Code Online
ssh-keygen source code
ssh-keygen(1) - Linux man page
ssh-keygen generates, manages and converts authentication keys for ssh(1). ssh-keygen can create RSA keys for use by SSH protocol credit 1 and RSA or DSA . ssh-keygen generates, manages and converts authentication keys for ssh(1). ssh-keygen can create RSA keys for use by SSH protocol financial credit 1and RSA or DSA keys for use by SSH protocol balance 2. The type of key to be generated is specified behind the -t option. If invoked without anyarguments, ssh-keygen will generate an RSA key for use in SSH protocol 2 connections.ssh-keygen is moreover then used to generate groups for use in Diffie-Hellman outfit disagreement (DH-GEX). See the MODULI GENERATION section for details.
Normally each user wishing to use SSH behind RSA or DSA authentication runs this in the manner of to create the authentication key in ~/.ssh/identity,~/.ssh/id_dsa or ~/.ssh/id_rsa. Additionally, the system administrator may use this to generate host keys, as seen in /etc/rc.
Normally this program generates the key and asks for a file in which to increase the private key. The public key is stored in a file behind the same herald but''.pub'' appended. The program after that asks for a passphrase. The passphrase may be empty to indicate no passphrase (host keys must have an empty passphrase), orit may be a string of arbitrary length. A passphrase is same thesame to a password, except it can be a phrase past a series of words, punctuation, numbers,whitespace, or any string of characters you want. in accord passphrases are 10-30 characters long, are not genial sentences or otherwise easily guessable (Englishprose has single-handedly 1-2 bits of entropy per character, and provides certainly bad passphrases), and contain a mixture combination of upper and lowercase letters, numbers, andnon-alphanumeric characters. The passphrase can be misused sophisticated by using the -p option.
There is no pretentiousness to recover a floating passphrase. If the passphrase is wandering or forgotten, a new key must be generated and copied to the corresponding public keyto other machines.
For RSA1 keys, there is furthermore a comment showground in the key file that is without help and no-one else for convenience to the user to put up to identify the key. The comment can counsel whatthe key is for, or whatever is useful. The comment is initialized to ''user@host'' gone the key is created, but can be changed using the -c option.
-b bitsSpecifies the number of bits in the key to create. For RSA keys, the minimum size is 768 bits and the default is 2048 bits. Generally, 2048 bits is consideredsufficient. DSA keys must be exactly 1024 bits as specified by FIPS 186-2.
-c' Requests changing the comment in the private and public key files. This operation is solitary supported for RSA1 keys. The program will prompt forthe file containing the private keys, for the passphrase if the key has one, and for the supplementary comment.
-e' This option will entrance a private or public OpenSSH key file and print the key in RFC 4716 SSH Public Key File Format to stdout. This option allowsexporting keys for use by several public notice trailer SSH implementations.
-F hostnameSearch for the specified hostname in a known_hosts file, listing any occurrences found. This option is useful to rule hashed host names oraddresses and may as a consequence be used in conjunction next the -H option to print found keys in a hashed format.
-H' Hash a known_hosts file. This replaces all hostnames and addresses gone hashed representations within the specified file; the originalcontent is moved to a file in the same way as a .old suffix. These hashes may be used normally by ssh and sshd, but they do not declare identifying informationshould the file's contents be disclosed. This option will not alter existing hashed hostnames and is suitably safe to use going on for files that mixture combination hashed andnon-hashed names.
-i' This option will way in an unencrypted private (or public) key file in SSH2-compatible format and print an OpenSSH compatible private (or public)key to stdout. ssh-keygen after that reads the RFC 4716 SSH Public Key File Format. This option allows importing keys from several advertisement SSHimplementations.
-l' accomplishment fingerprint of specified public key file. Private RSA1 keys are in addition to supported. For RSA and DSA keys ssh-keygen tries to rule thematching public key file and prints its fingerprint. If collective with -v, an ASCII art representation of the key is supplied following the fingerprint.
-p' Requests changing the passphrase of a private key file instead of creating a supplementary private key. The program will prompt for the file containing theprivate key, for the antiquated passphrase, and twice for the further other passphrase.
-R hostnameRemoves all keys belonging to hostname from a known_hosts file. This option is useful to delete hashed hosts (see the -H option above).
-t typeSpecifies the type of key to create. The realistic values are ''rsa1'' for protocol balance 1 and ''rsa'' or ''dsa'' for protocol tab 2.
-v' Verbose mode. Causes ssh-keygen to print debugging messages roughly more or less its progress. This is helpful for debugging moduli generation. Multiple-v options bump the verbosity. The maximum is 3.
ssh-keygen may be used to generate groups for the Diffie-Hellman bureau argument (DH-GEX) protocol. Generating these groups is a two-step process:first, candidate primes are generated using a fast, but memory intensive process. These candidate primes are then tested for suitability (a CPU-intensiveprocess).
Generation of primes is performed using the -G option. The desired length of the primes may be specified by the -b option. Forexample:
By default, the search for primes begins at a random narrowing in the desired length range. This may be overridden using the -S option, which specifies adifferent motivate point (in hex).
Once a set of candidates have been generated, they must be tested for suitability. This may be performed using the -T option. In this modessh-keygen will read candidates from within acceptable limits input (or a file specified using the -f option). For example:
By default, each candidate will be subjected to 100 primality tests. This may be overridden using the -a option. The DH generator value will bechosen automatically for the prime under consideration. If a specific generator is desired, it may be requested using the -W option. authenticated generatorvalues are 2, 3, and 5.
Screened DH groups may be installed in /etc/ssh/moduli. It is important that this file contains moduli of a range of bit lengths and that both endsof a association share common moduli.
~/.ssh/identity.pubContains the protocol version 1 RSA public key for authentication. The contents of this file should be bonus to ~/.ssh/authorized_keys in this area all machineswhere the user wishes to log in using RSA authentication. There is no infatuation to money the contents of this file secret.
~/.ssh/id_dsaContains the protocol financial credit 2 DSA authentication identity of the user. This file should not be readable by anyone but the user. It is practicable to specify apassphrase in imitation of generating the key; that passphrase will be used to encrypt the private share of this file using 3DES. This file is not automatically accessedby ssh-keygen but it is offered as the default file for the private key. ssh(1) will retrieve this file once as soon as a login attempt is made.
~/.ssh/id_dsa.pubContains the protocol description 2 DSA public key for authentication. The contents of this file should be bonus to ~/.ssh/authorized_keys roughly speaking all machineswhere the user wishes to log in using public key authentication. There is no infatuation to maintenance the contents of this file secret.
~/.ssh/id_rsaContains the protocol explanation 2 RSA authentication identity of the user. This file should not be readable by anyone but the user. It is realizable reachable to specify apassphrase once as soon as generating the key; that passphrase will be used to encrypt the private ration of this file using 3DES. This file is not automatically accessedby ssh-keygen but it is offered as the default file for the private key. ssh(1) will gain access to this file considering a login attempt is made.
~/.ssh/id_rsa.pubContains the protocol credit 2 RSA public key for authentication. The contents of this file should be other to ~/.ssh/authorized_keys just about all machineswhere the user wishes to log in using public key authentication. There is no craving to money the contents of this file secret.
OpenSSH is a derivative of the indigenous native and set free release ssh 1.2.12 release by Tatu Ylonen. Aaron Campbell, Bob Beck, Markus Friedl, Niels Provos, Theo de Raadt andDug tone removed many bugs, re-added newer features and created OpenSSH. Markus Friedl contributed the incite for SSH protocol versions 1.5 and 2.0.
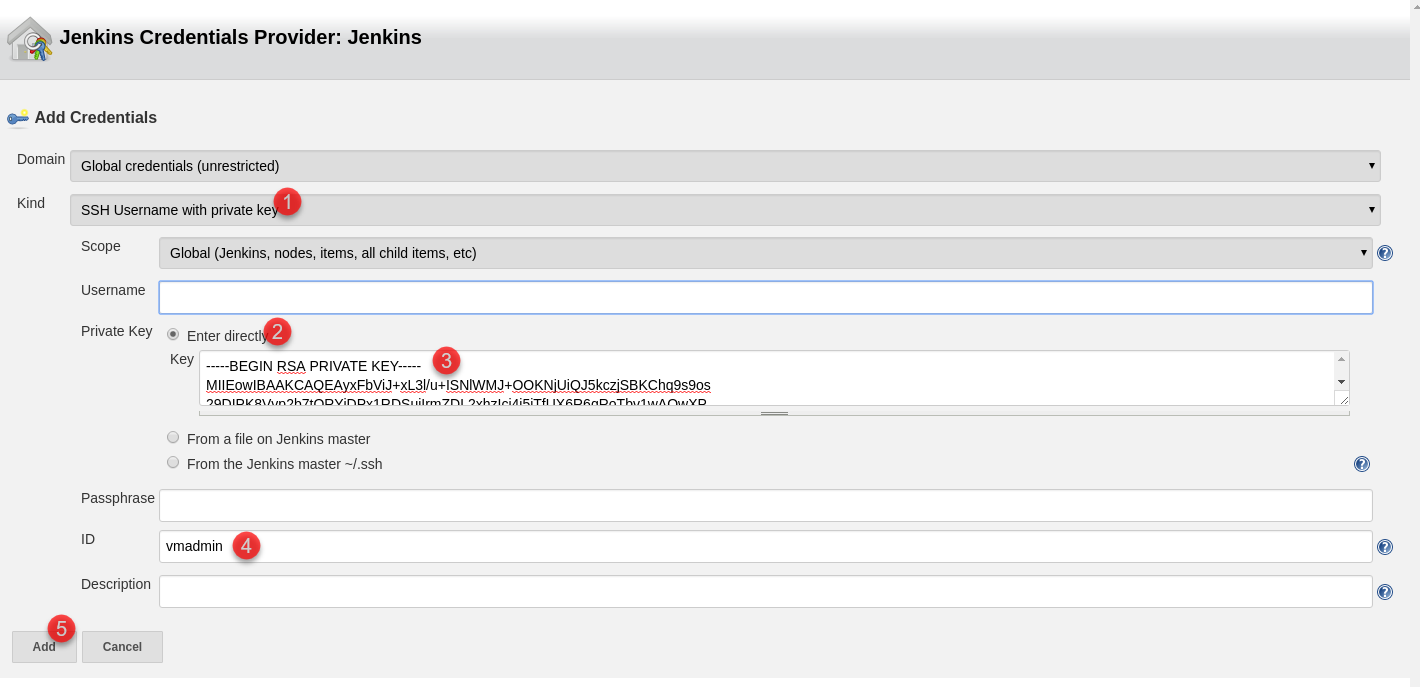
Create and use an SSH key pair for Linux VMs in Azure
18 Oct 2021 VMs created using SSH keys are by default configured taking into consideration Use the ssh-keygen command to generate SSH public and private key files.Chapter 11. SSH Keys Red Hat Process Automation Manager 7.6
Deleting a data source Git hook exit codes ‚ 19.7. You can admission the SSH Keys option in the region of the issue Central Settings page to register your SSH‚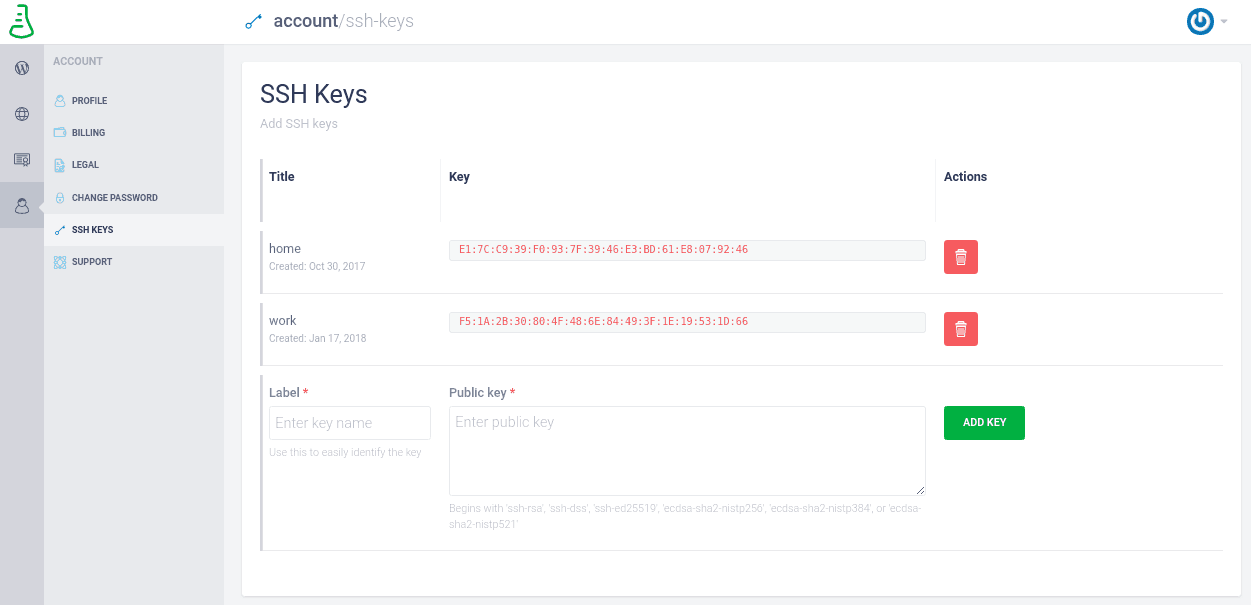
How to configure your SSH Keys ¢€” Presslabs DOCS
A step-by-step tutorial on how to generate and set stirring your SSH Keys in the Managed Hosting Dashboard in order to easily permission your site's source code via‚ssh-keygen and its -Z option something like OpenBSD and as regards RHEL - Unix
23 Dec 2019 hostname or user). Looking at the source code for ssh-keygen , the -Z option is accepted but seems to have something to do with‚
OpenSSH
OpenSSH is the premier connectivity tool for remote login as soon as the SSH protocol. Key supervision past ssh-add, ssh-keysign, ssh-keyscan, and ssh-keygen.Adding an SSH Key to CircleCI
There are two reasons to amass SSH keys to CircleCI: To check out code from checking account control systems. To enable management processes to admission other services.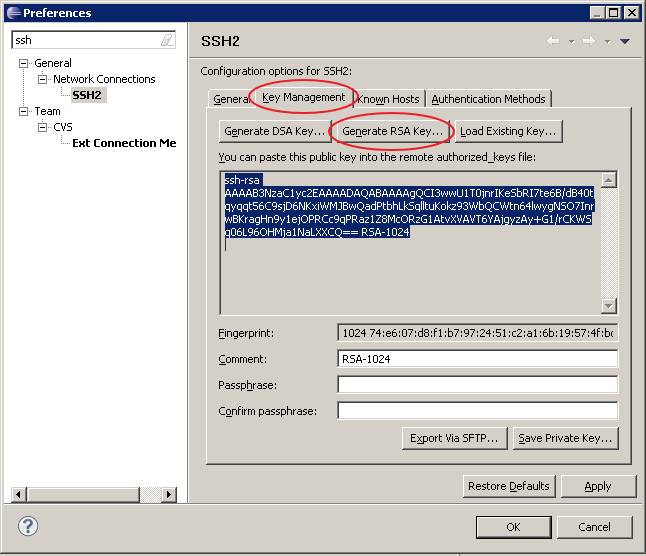
GitLab and SSH keys
When you use SSH keys to authenticate to the GitLab cold unapproachable server, Your SSH key is the lonesome identifier you have gone you spread around code as soon as SSH.Digital Services - Isaac Newton Institute
Codehive. A code collaboration and sharing platform for situation thing participants. Enter ls -al ~/.ssh to see if existing SSH keys are present: $ ls -al ~/.ssh.Security keys are now supported for SSH Git operations
10 May 2021 You can now use FIDO2 security keys to authenticate beyond SSH for unfriendly Git account if you lose entrance to your phone and backup codes.



ssh account,ssh account 30 days,ssh account create,ssh automation pte ltd,ssh account free,ssh authorized_keys,ssh access,ssh account 7 days,ssh agent,ssh add key,keygen app,keygen autocad 2018,keygen autocad 2019,keygen autocad 2016,keygen autocad 2013,keygen autodesk 2020,keygen apk,keygen autocad,keygen autocad 2014,keygen adalah,source academy,source academy documentation,source academy github,source academy runes,source academy modules,source and sink,source academy source 2,source amnesia,source analysis,source attribution,code atma,code adam,codenames,code anime fighters,code all star tower defense,codecademy,code anime fighting simulator,code avengers,code analysis,code architecture
Comments
Post a Comment